Let’s start with some examples
To examine the namespaces of a particular process using the procfs virtual filesystem, you can look at the /proc/[pid]/ns directory.
For example, to view the namespaces of the current shell process, you can do
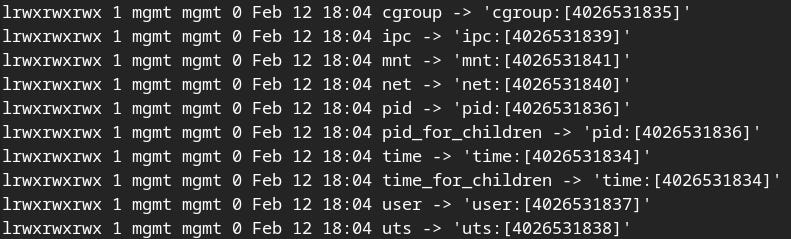
ls -l /proc/$$/ns
This will display a list of symbolic links, each representing a different namespace. The output will look similar to this:
Each symbolic link represents a specific namespace, and the numbers in square brackets are inode numbers that uniquely identify the namespace. If two processes have the same inode number for a particular namespace, it means they are in the same namespace for that resource.
From the above, we can see that there are 8 types of namespace: cgroup, ipc, mnt, net, pid, time, user, uts. We are going to look at each of them one by one in the later blog posts.
Let’s look at `user` namespace now.
User namespace
There are several ways that you can create new namespaces, but we are going to stick with the one used most for this kind of exploratory exercise: i.e “unshare”. You can look at “man 1 unshare” for more info.
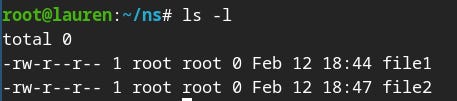
A classical example would be to run command as a “fake" root, running “unshare —map-root-user bash'“ will make you landed on “root” like this : showing root as user and having id 0
You can even touch a file and the file would be owned by “root”
But once you exit from this shell and you will see that the root user in the previous shell is just mapped on the original user outside of that newly created namespace
If we look at the man page, we found this is meant to a QoL flag for some use cases
This makes it possible to conveniently gain capabilities needed to manage various aspects of the newly created namespaces (such as configuring interfaces in the network namespace or mounting filesystems in the mount namespace) even when run unprivileged …
Namespace is a powerful feature in Linux and we will continue look at more examples and the other types of namespace later